
UTAR Faculty of Information and
Communication Technology (FICT),
Division of
Programme Promotion (DPP) and Department of
Soft Skills Competency (DSSC) organised a webinar titled “How to Surf
Safely Without Being Eaten by Sharks – Internet Security 101” via Google
Meet on 4 June 2020.
A
lot of cyber-attacks have been happening recently. They are usually aimed at
accessing, modifying and destroying information, stealing money from users
or interrupting business operation. The purpose of the webinar is to raise
awareness of internet security among targeted secondary school students, as
well as to improve their knowledge on how to safeguard their personal
information.
Speaking at the webinar was a tutor from FICT, Tan Lyk Yin. Tan has been
teaching networking and communication at UTAR for several years. The
one-hour webinar saw more than 170 participants.
Tan kick-started the webinar by giving the participants some survey
questions regarding internet security via kahoot.it. Then, she gave examples
regarding the impacts of cyber-attack and the monetary loss caused by it.
“Yahoo! was a web service company once worth more than 100 billion in the year 2001 and was sold to Verizon Media for 4.48 billion in 2016 after a massive data breach that caused data leaking including email address, name, telephone number, date of birth and also encrypted password in 2013 and 2014,” said Tan.
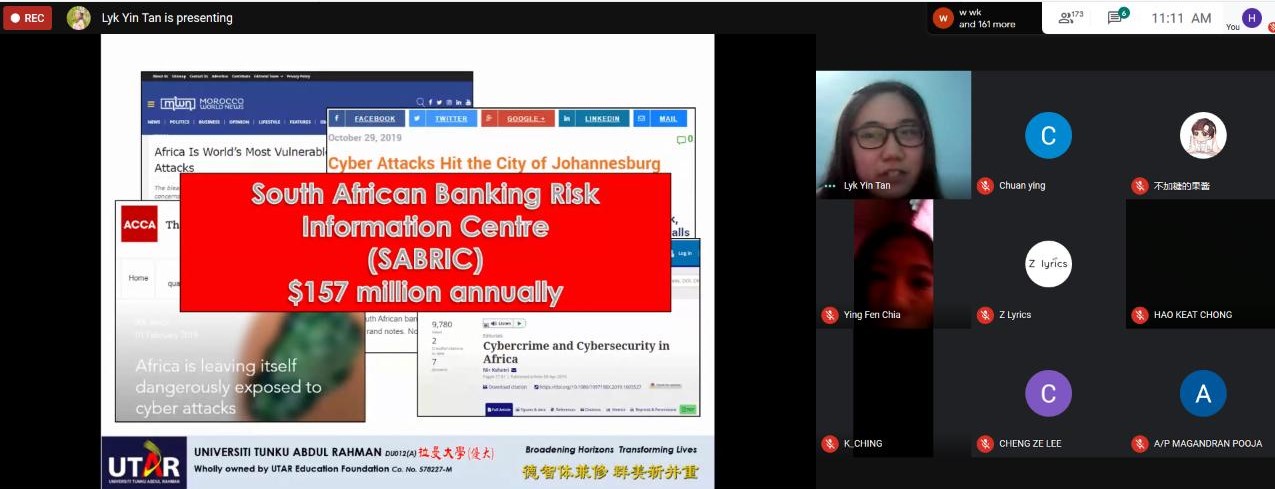
Tan said, “Cyber-attack also impacts the economy of a country.” According to
the information given by the South African Banking Risk Information Centre
(SABRIC), South Africa loses 157 million annually due to cyber-attacks. Tan
explained, “Banks and companies in South Africa are highly targeted by
hackers because they cannot defend themselves as their technology
development is not as fast as other countries.”
Tan also addressed three major reasons for the occurrence of cyber-attacks.
The first type of cyber-attack is done by hackers who are hired by an
organisation to attack their competitors. The second type of cyber-attack is
caused by hackers who steal data to sell to a third party, such as scammers
in order to get money. The last type of cyber-attack is performed by those
who crack games, software or songs from an original source to make them
available on certain websites. The songs, games and software might contain
malware or virus which could cause a data breach.
She advised, “We should download all the stuff from a trusted source or
their official website because some free downloaded software, songs or games
might contain a virus or malware that could harm your PC.” She then
explained, “The attacker seeks some type of benefits from the attack.”
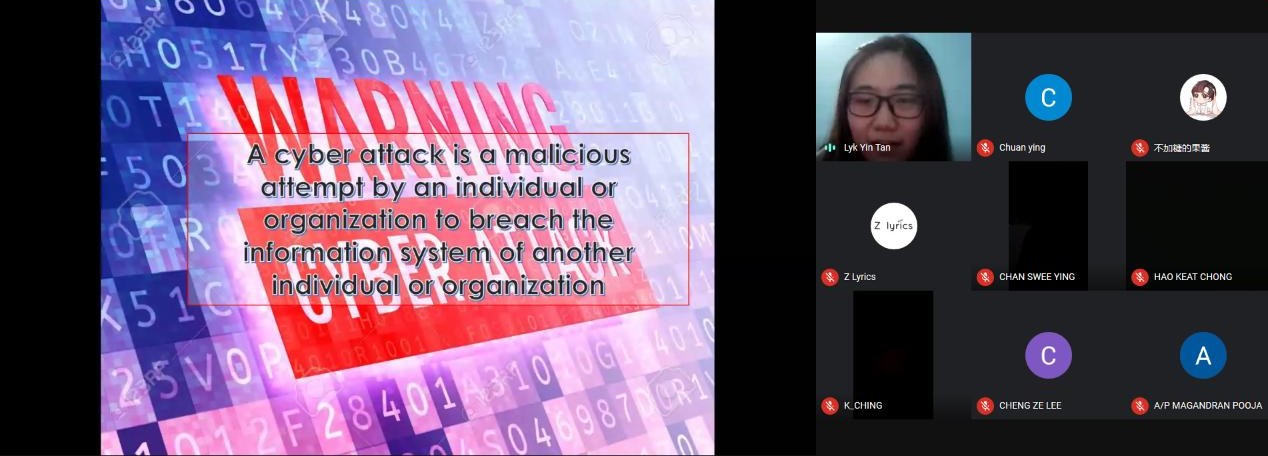
Tan explaining the
meaning of “cyber-attack”
Speaking of how to surf the internet safely without
being attacked by a hacker, Tan provided several suggestions. “Always
remember to log out and clear all the browsing data after you use a public
terminal or shared computer.”
“Sometimes, some computers might contain
pre-installed malware, so you can either use key encryption software or
anti-malware program to keep your data safe. To keep your password safe, you
could search for an online keyboard which is available on the internet to
type the password. After you have typed the password using the online
keyboard, copy the password and paste it on the website where you want to
log in.”
“Do not grant permissions to any application or game
on social media without checking. Try to secure your password by using a
combination of uppercase and lowercase letters, symbols, and numbers. Avoid
using the same password for different platforms.”
Besides, Tan also discouraged the participants from
posting any information in social media such as their location, credit card
number or any other sensitive information. She stressed on the fact that
nothing is secured on the internet.
The webinar ended with a demo on how a hacker obtains a user’s personal data when the user access to any website.
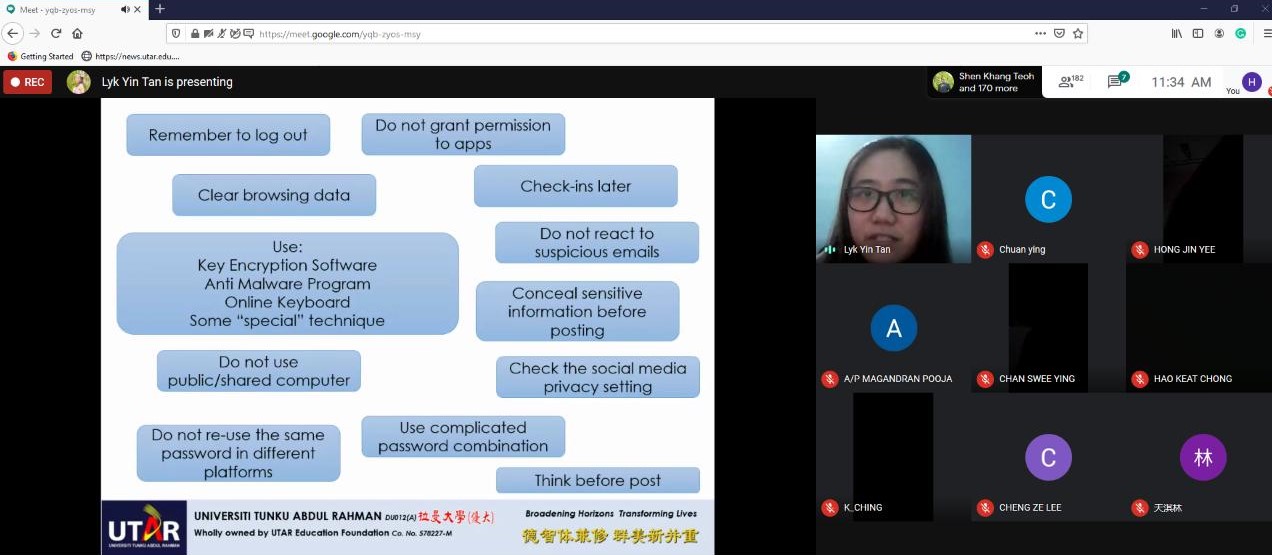
Tan suggesting methods to avoid being attacked by hackers
Students were encouraged to enrol in technology communication and networking courses provided by UTAR
![]()
![]()
Wholly owned by UTAR Education Foundation Co. No. 578227-M LEGAL STATEMENT TERM OF USAGE PRIVACY NOTICE